It is useful to learn how to use iptables to enable port forwarding and perform basic Network Address Translation (NAT) and Dynamic Port Address Translation (PAT). Below is a diagram and rules for a basic port forwarding example through the iptables from the internet to the Windows Machine in KVM.
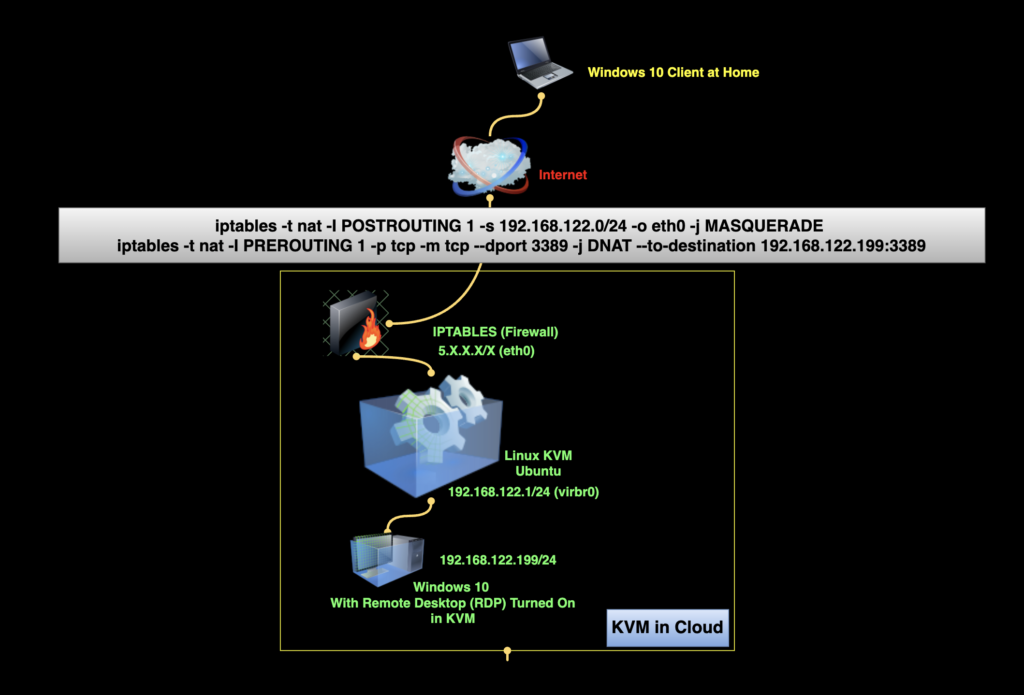
The first rule evaluate the outgoing packet after routing/forwarding is perform and check if the source ip -s is from the KVM LAN 192.168.122.0/24. If it is not it will go through the rest of the Chain and Table. If it is Yes then it will be forwarded -j to the -o eth0 outgoing/outside interface eth0. MASQUERADE will perform the Dynamic Port Address Translation (PAT) to transform the source address to the IP Address of the Outside interface (5.x.x.x) and routed out to the internet.
Change the -s to your actual LAN subnet and -o to the actual interface in your environment.
This command is use for outgoing traffic.
iptables -t nat -I POSTROUTING 1 -s 192.168.122.0/24 -o eth0 -j MASQUERADE The second rule is perform when the packet reaches the outside interface (It can be for any interface). Before routing/forwarding is perform, the packet will be evaluated. it checks for matches against TCP protocol -p tcp -m tcp if Yes, then it looks for destination port 3389. If the packet is TCP base going to port 3389 it will then forward/jump -j to 192.168.122.199:3389 which is the Windows machine running in KVM listening on port 3389 RDP.
iptables -t nat -I PREROUTING 1 -p tcp -m tcp --dport 3389 -j DNAT --to-destination 192.168.122.199:3389I have done a query in chatgpt and I think it does a good job explaining the rule.