Demo on Nmap Target Specific Commands.
Target Specific
| Switch | Example | Description |
|---|---|---|
| nmap 192.168.33.200 | Scan a single IP | |
| nmap 192.168.33.200 192.168.33.203 | Scan specific IPs | |
| nmap 192.168.33.1-254 nmap 192.168.33.* | Scan a range | |
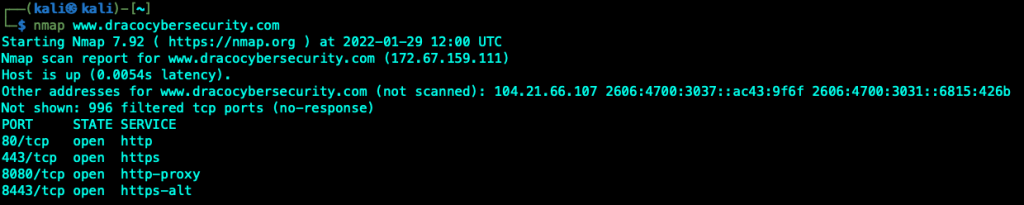
| nmap www.dracocybersecurity.com | Scan a domain | |
| nmap 192.168.33.0/24 | Scan using CIDR notation | |
| -iL | nmap -iL targets.txt | Scan targets from a file |
| -iR | nmap -iR 100 | Scan 10 random hosts |
| –exclude | nmap 192.168.33.* –exclude 192.168.33.88 192.168.33.203 | Exclude listed hosts |
The new Windows Server 2022 seems to be able to detect potential Host discovery from nmap, therefore even thou the server is up we are unable to get any response from the scan.
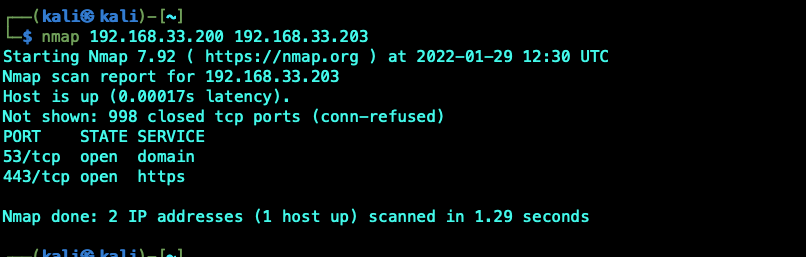
Scanning 2 specific host, we are able to detect the DNS server in my lab but not the Windows Server 2022.
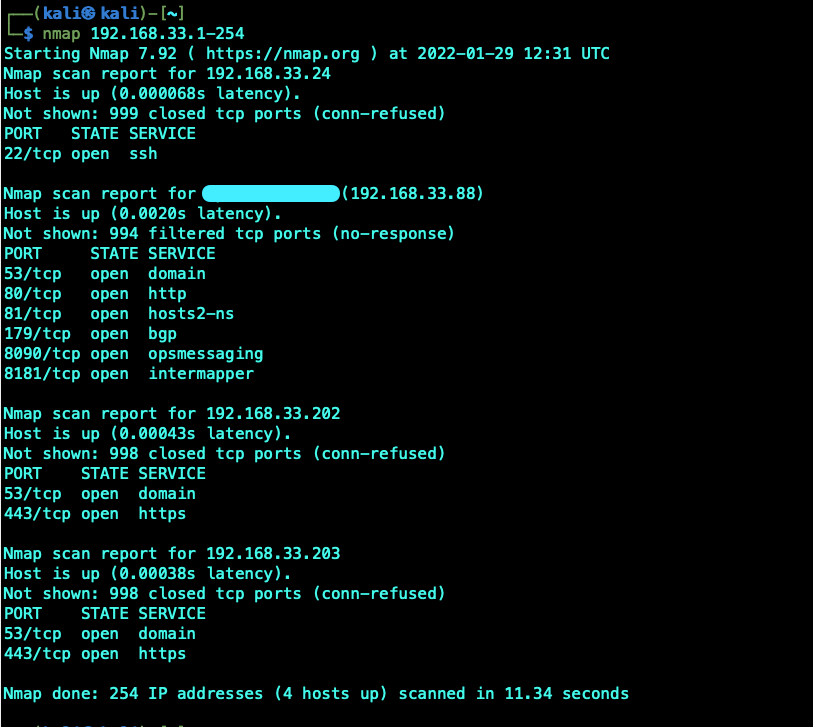
Scanning the whole range returns 4 hosts. There are a couple of Windows Server 2022 that did not show up in the scan.
It is important to note that you must never scan target machine that does not belong to you without prior consent. This tutorial is mend for you lab / testing environment.
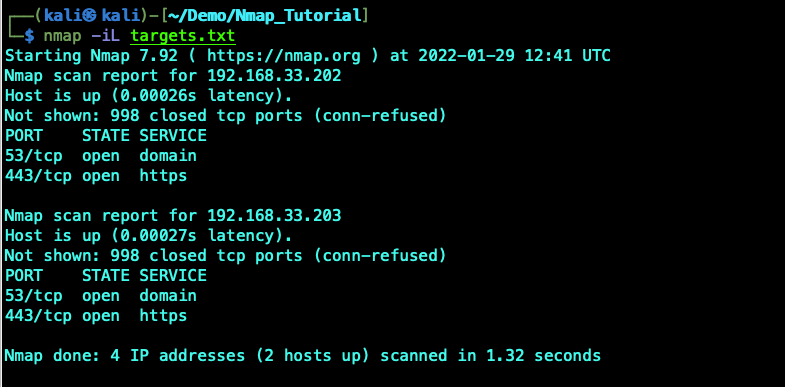
To scan a list of targets create a targets.txt file and then use the -iL switch to scan the targets define in the files. This is useful in combination with a quick scan to quickly output the list of target servers and then us the target list to do a more in depth scan. Below is a sample of the targets.txt file and the scan.
The –exclude switch is useful if you want to exclude servers that you want to exclude from your scan. In a lot of situation the cyber criminal may exclude scanning the Firewall or IPS to avoid detection. You can exclude 1 or more IP addresses from your scan.

nmap -iR <num> itself will Randomly scan the internet and should not be carried out. It can be use in a control environment for scanning the organization own public IP.
